File Integrity Monitoring
No organization wants to contend with costly service outages or security breaches. But when devices are configured improperly, that is exactly what happens.
In an attempt to alleviate these issues, organizations rely on File Integrity Monitoring (FIM). Not only is this an essential security practice, but is also mandated by several compliance standards.
Did it Change? vs. Is it Correct?
File integrity monitoring solutions take a baseline (or snapshot) of the data on each system (files, permissions settings, etc.) under the erroneous assumption that each system is in a known good state. Monitored systems are then evaluated, detecting and reporting deviations from the established baseline.
SignaCert provides the only FIM solution that enables you to easily determine whether critical applications are consistently deployed across a set of systems.
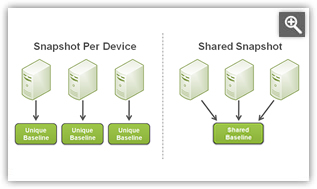
The fundamental problem with FIM solutions is that separate baselines are created for each monitored system. Not only is this a time-consuming and resource-intensive process, but it doesn't address the “integrity” aspect of file integrity monitoring. When a change is reported, all you know is that the system is different today than it was yesterday. What you need to know is whether systems have drifted from approved standards.
SignaCert's Next-Generation FIM
In addition to supporting the creation a unique baseline per device, SignaCert also allows for baselines that are shared by multiple systems. This goes beyond mere change detection to ensure that systems are aligned to your enterprise standards. With SignaCert's FIM solution you can easily determine whether critical applications are consistently deployed across a set of systems, or whether all of the critical components of an infrastructure service (web, service layer, database, etc.) are deployed consistently throughout a server farm. SignaCert is the only FIM-based solution on the market today capable of providing these answers.
SignaCert's FIM solution addresses the following compliance requirements (among others):
-
NIST 800-53
CP-9: "...protects the confidentiality and integrity of the backup information."
SI-4: "Deploy file-integrity monitoring software to alert personnel to unauthorized modification of critical system files, configuration files, or content files..."
SI-7: "The information system detects unauthorized changes to software and information..." -
PCI DSS
10.5.5: "Use file integrity monitoring and change detection software on logs to ensure that existing log data cannot be changed without generating alerts..."
11.5: "Deploy file-integrity monitoring software to alert personnel to unauthorized modification of critical system files, configuration files, or content files..." -
COBIT
DS 9.2: "IT management should be ensured that a baseline of configuration items is kept as a checkpoint to return to after changes."
DS 11.30: "Management should ensure that the integrity and correctness of the data kept on files and other media is checked periodically." -
HIPAA
164.312: "Implement policies and procedures to protect electronic protected health information from improper alteration or destruction."